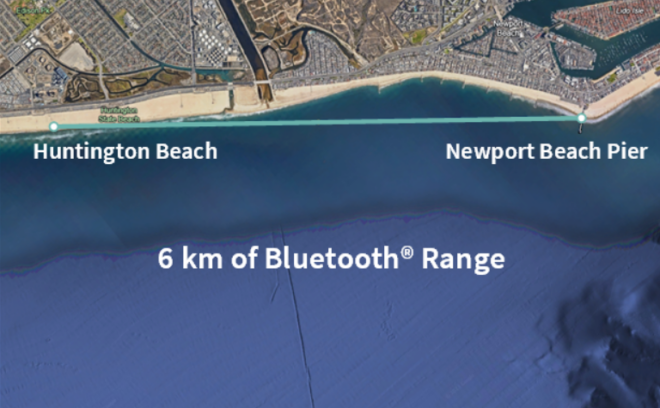
Bluetooth® enabled devices are capable of achieving highly reliable communication in even the most challenging circumstances. At every layer, Bluetooth technology was designed with reliability in mind and has adopted a number of techniques to lower the probability of suffering from interference.
Recently, Martin Woolley, developer relations manager with the Bluetooth Special Interest Group (SIG), released a paper on Understanding Reliability in Bluetooth Technology. In this deep dive into Bluetooth reliability, Woolley explains how Bluetooth technology can build reliable connections despite the inherent unreliable nature of radio.
Below is an excerpt from that section of Woolley’s paper.
Creating Reliability From Unreliable Foundations
Bluetooth® technology uses radio, and radio is unreliable. But Bluetooth communication works very well, so how is this apparent contradiction to be explained? The answer lies in numerous aspects of the design of the Bluetooth communication system, including its use of radio and its protocols.
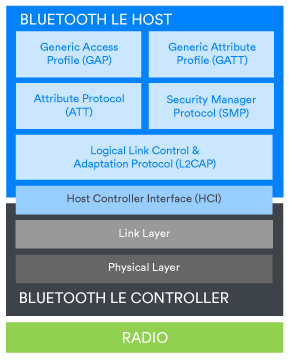
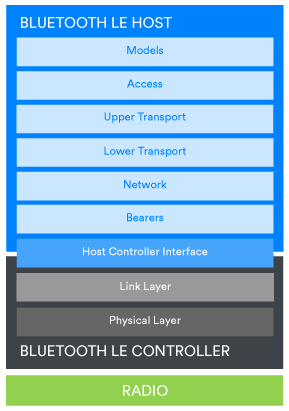
Bluetooth technology is a modular system and more than one configuration of stack is possible.
Smartphones and connectable peripheral devices will include a Bluetooth Low Energy (LE) controller with a host component that supports the Generic Access Profile (GAP) and Generic Attribute Profile (GATT) and protocols such as the Attribute Protocol (ATT) and Security Manager Protocol (SMP). Figure 3a shows this stack configuration.
A Bluetooth mesh device will also contain a Bluetooth LE controller, but the host part will contain the layers of the Bluetooth mesh networking stack. Figure 3b depicts a Bluetooth mesh stack.
Whatever the stack configuration, each layer has clearly defined responsibilities and a means of passing data to the adjacent layers above and below. Features of Bluetooth technology which mitigate or reduce the probability of certain types of potential reliability problems exist in various parts of the stack. Some such mechanisms apply to all possible uses of Bluetooth technology, while some of them apply to only particular scenarios.
Generally Applicable Features and Mitigation Techniques
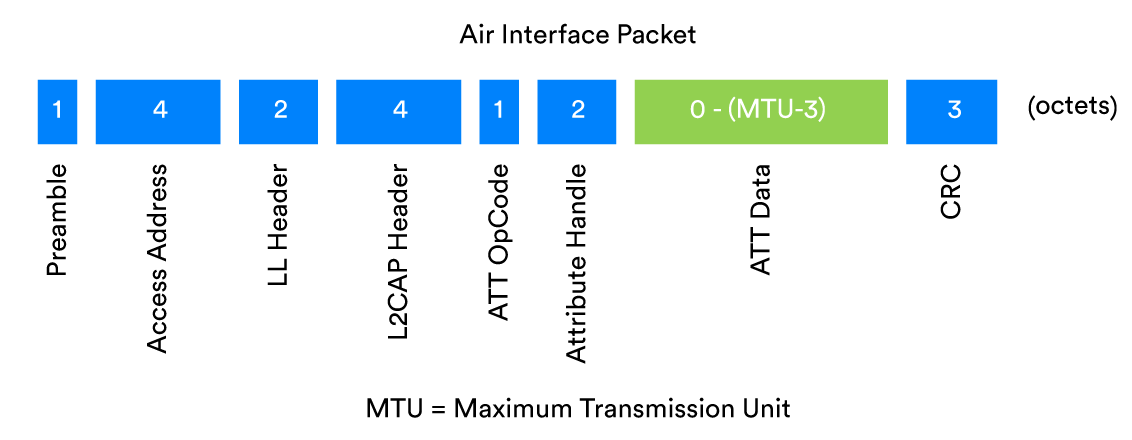
We’ll start with a guided tour of the reliability enhancing features of Bluetooth® technology that are generally applicable in all scenarios. Figure 4 shows an example Bluetooth air interface packet and will be referred to.
The Bluetooth Modulation Scheme
Reliability in Bluetooth® technology starts with the most fundamental of issues, concerning exactly how radio is used as a carrier for digital data. In the Bluetooth stack, these issues are dealt with in the physical (PHY) layer.
One of the primary problems that the physical layer must deal with is to be able to recognize Bluetooth radio transmissions and extract the data encoded in a signal correctly. This is an absolutely fundamental step on the road to reliability.
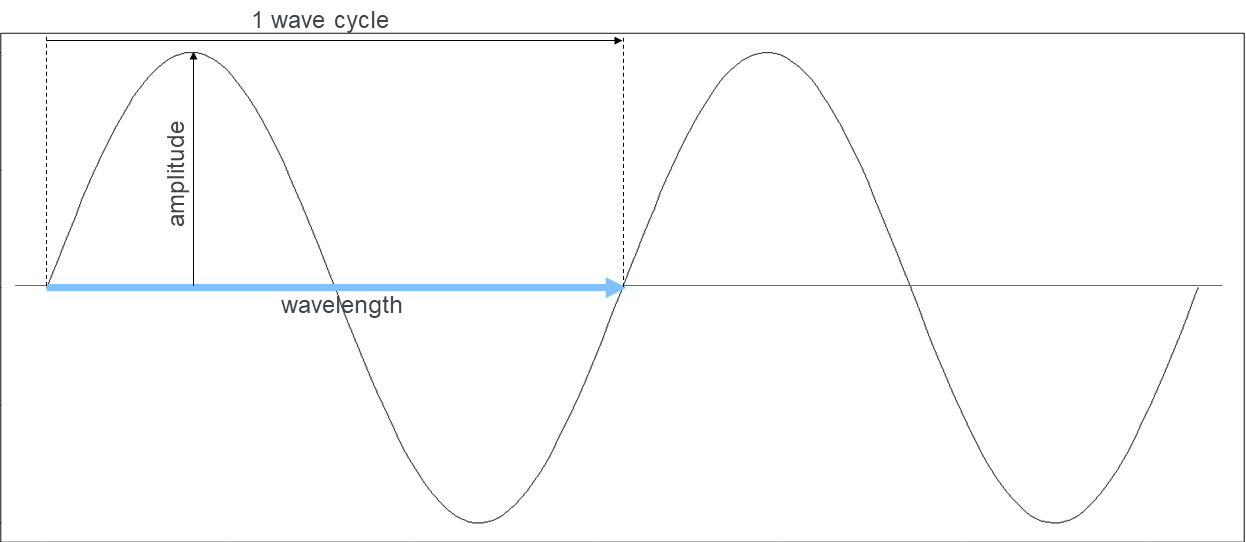
Radio is an analogue, physical phenomenon. Physicists typically model radio signals in terms of waves. Radio waves possess electromagnetic energy and have a collection of fundamental properties, including amplitude, wavelength, and frequency. These concepts are illustrated in Figures 5 and 6. As defined previously, strategies which use the fundamental properties of waves in some way to encode information are called modulation schemes. There are many modulation schemes. Some use the changing amplitude of a signal; some encode information using radio phase and some use frequency changes.
When reliability is an important design goal for a radio communication system, some modulation schemes are better than others. Amplitude-based modulation schemes are somewhat susceptible to interference due to noise, whereas frequency-based schemes are less vulnerable in this respect.
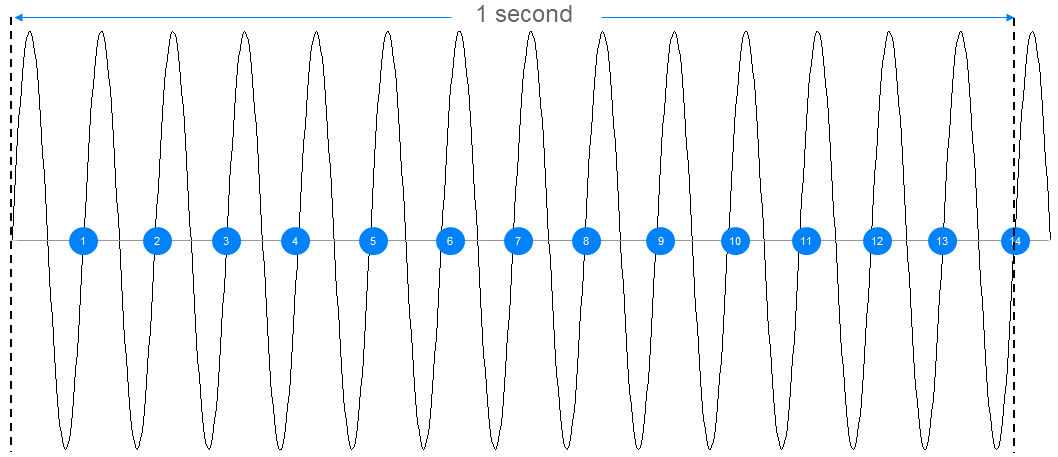
Bluetooth® technology uses a special binary frequency-shift keying modulation scheme called Gaussian Frequency Shift Keying (GFSK). It’s a binary modulation scheme because each symbol represents only one bit with a value of either zero or one.
Binary frequency shift keying encodes digital data by selecting a central frequency known as the carrier and then shifting it up by a given frequency deviation to represent a 1 or down by the same frequency deviation to represent a 0. The minimum size of the frequency deviation that is permitted is specified in the Bluetooth Core Specification and depends on the selected symbol rate, which is either 1 or 2 mega-symbols per second (Msym/s) in Bluetooth LE. For the 1 Msym/s symbol rate, a minimum frequency deviation of 185 kHz is specified, whereas for the faster symbol rate, the minimum frequency deviation is 370 kHz. These values were chosen carefully to help make the recognition of encoded 1s and 0s in a signal reliable.
Frequency shift keying (FSK) modulation schemes, by definition, involve a frequency change each time the symbol value changes. An abrupt, near-instantaneous change of frequency will generate noise, and noise causes interference. Furthermore, in real circuits, there is the possibility of spectral leakage where the signal spills over, unintentionally, into other frequencies, making the task of decoding it at the receiver all the more difficult.
Bluetooth technology reduces interference through its use of a superior FSK modulation scheme, GFSK. The Gaussian aspect of GFSK modifies the standard FSK approach by including a filter which causes frequency transitions to be smoothed and therefore less noisy and the spectral width to be narrower, reducing the potential for interference with other frequencies.
Preamble
The first field in all Bluetooth® LE packets is called the preamble. It is 8 bits long and contains an alternating pattern of binary ones and zeroes. Its purpose is to provide the receiver with material it can use to find the frequencies being used to encode digital ones and zeroes in the remainder of the packet. It is also used by the radio’s automatic gain control which optimises the signal strength. Accurately establishing the frequencies used in a signal and setting the radio’s parameters to an optimal state is the first step in ensuring reliable receipt of a packet.
![]()
FEATURED
How Bluetooth® Technology Makes Wireless Communication Reliable
Learn about the challenge of wireless interference and the techniques Bluetooth technology uses to overcome it.
Access Address
When the Bluetooth® controller is listening for data on a channel, it will receive all radio signals within the frequency range defined by that channel. Received signals may be:
-
- Bluetooth packets sent to this device
- Bluetooth packets which are not intended for this device
- Packets relating to other wireless communications technologies which are operating in the same ISM band and using frequencies in the Bluetooth radio channel currently being scanned
- Background noise
The Bluetooth controller must be able to distinguish between these signals and accurately pick out those that encode Bluetooth packets sent to this device. Anything else must be ignored.
All Bluetooth packets contain a 32-bit access address which allows signals that are almost certainly Bluetooth to be quickly picked out at the earliest opportunity, and other signals to be immediately discarded.
There are two types of access address. The advertising access address is a fixed value of 0x8E89BED6 which most advertising packets use. This value was chosen because it has good correlating properties. Correlation is the mathematical procedure used to recognize specific patterns in a signal.
Packets exchanged during communication between two connected devices contain an access address with a value assigned by the link layer which uniquely identifies all packets relating to that connection. These generated access address values are largely random but subject to additional rules which are designed to increase the reliability of recognizing access addresses correctly.
Packets relating to distinct periodic advertising chains and to distinct Broadcast Isochronous Streams (BIS) each have a unique access address. The access address allows signals which are relevant to the receiving device to be selected. It is the responsibility of the Bluetooth stack’s Link Layer to check access addresses.
The probability of mistaking random background electromagnetic noise for a Bluetooth signal is extremely small, thanks to the 32-bit length of the access address. In the unlikely event that the pattern of random background noise matches an access address which is relevant to the receiver, further bit stream processing will quickly determine that it is not a valid Bluetooth packet.
Quickly selecting only relevant signals, and discarding others, is another key step in Bluetooth receiver operation which contributes to reliable communication.
The Cyclic Redundancy Check (CRC)
All Bluetooth packets contain a Cyclic Redundancy Check (CRC) field which appears at or near the end of the packet. CRCs are a commonly used mechanism for detecting cases where transmitted data has been unintentionally changed due to issues like collisions.
When a new packet is formulated by the link layer, a CRC value is calculated by applying the CRC algorithm to the other bits in the packet. The resultant 24-bit value is then added to the packet. On receiving a packet, the link layer in the receiving device recalculates the CRC and compares the result with the CRC value included in the received packet. If the two values are not the same, it is concluded that one or more bits in the transmitted packet have been changed and the packet is discarded.
It should be noted that the CRC is not a security mechanism, since a packet could be deliberately altered and the CRC easily recalculated.
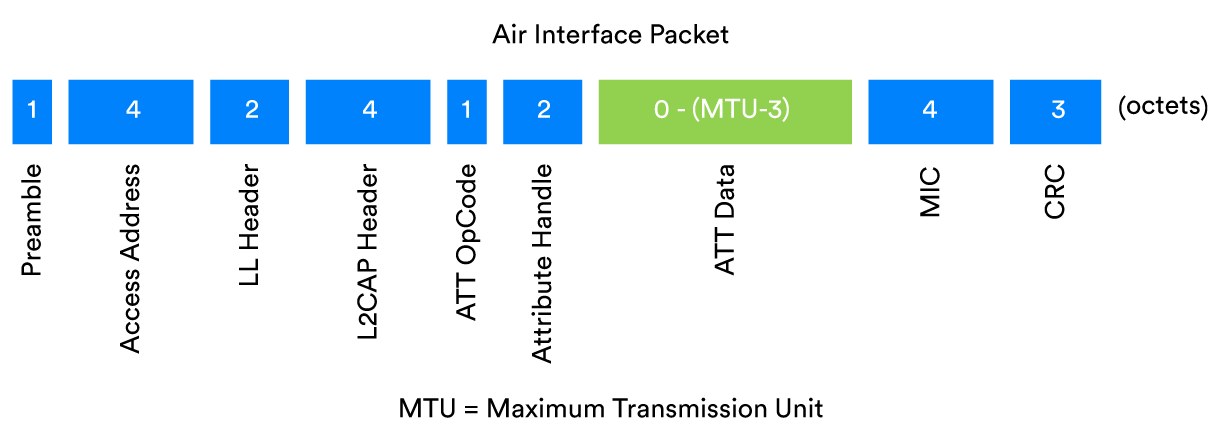
The Message Integrity Code (MIC)
Bluetooth® LE packets may be encrypted. All encrypted packets include a field called the Message Integrity Check (MIC). The MIC is, in fact, a message authentication code, but since the acronym MAC has other uses in the field of communications, in the Bluetooth specification, MIC is used.
The MIC is not a reliability feature per se. It is a security feature whose purpose is to enable the detection of attempts to deliberately tamper with the contents of a packet. But since part of our informal definition of reliability is that the data transmitted should be the data received and we acknowledge that changes may be unintentional or deliberate, we include it here for completeness.
After all, can insecure communication ever really be thought of as being reliable?
Spread Spectrum
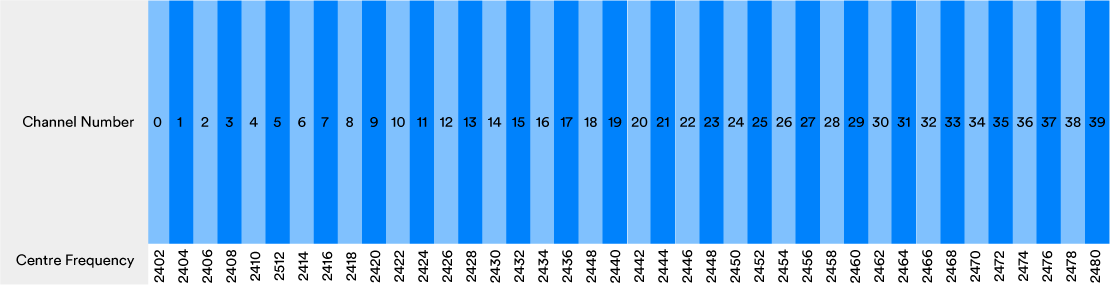
Bluetooth® technology uses the 2.4GHz ISM radio band. 2.4 GHz ISM does not define a single frequency, but rather it defines a range of frequencies, in this case starting at 2400 MHz and ending at 2483.5 MHz. When used with Bluetooth LE, this frequency range is divided into 40 channels, each 2 MHz wide. Bluetooth BR/EDR divides it into 80 channels of 1 MHz width.
Each channel is numbered, starting at channel zero. Channel zero has a centre frequency of 2402 MHz, leaving a gap of 1 MHz between the lowest frequency delimiting channel zero and the start of the ISM 2.4 GHz band. Channel 39 has a centre frequency of 2480 MHz, which leaves a gap of 2.5 MHz to the end of the ISM 2.4 GHz band.
Figure 8 depicts the division of the ISM band into radio channels for use by Bluetooth LE. Note that channel number always ascends in a contiguous sequence from 0 to 39 whereas a channel index, which we will cover in section 5.2.2, is assigned to the set of ISM channels in a slightly different way.
Communication of data over Bluetooth technology makes use of more than one radio channel. Using multiple radio channels makes Bluetooth communication highly reliable in busy radio environments where collisions and interference are likely to occur.
The use of multiple frequencies in this way is called a spread spectrum technique and Bluetooth can be said to be a spread spectrum radio communications technology. The details of how spread spectrum techniques are employed vary in a number of different situations and the topic will be reexamined in sections 5.2, 5.3, and 5.4.
Addressing Coexistence and Collocation Issues
The use of the same radio band by a number of different radio technologies at the same time poses potential challenges. It is possible for one technology to interfere with the transmissions of another technology, notably through the occurrence of collisions (see 3.1). Collectively, such issues are known as coexistence problems. Bluetooth® technology, Wi-Fi, cordless DECT phones, and even microwave ovens all operate in the 2.4 GHz ISM band, and so the potential for coexistence problems between these technologies and device types exists.
Coexistence issues are primarily addressed in Bluetooth through the use of spread spectrum techniques. Even greater reliability is achieved when two devices are connected, through the particular way in which spread spectrum techniques are used in Bluetooth in that scenario and this will be explored in section 5.2.
Collocation is the term used to describe the existence of more than one radio within the same device, each supporting a different communications technology or set of technologies. There is scope for interference between the different radios in a device. A Long-Term Evolution (LTE) radio, as used in 4G mobile phone systems, can operate in frequency bands that are adjacent to the 2.4 GHz ISM band, which gives rise to potential problems such as preventing one radio from receiving whilst the other is transmitting. Most collocation issues fall outside of the scope of the Bluetooth Core Specification itself, but advice to implementers is provided. Mitigating measures include the use of filters which reduce interference between radios and radio time-slot scheduling considerations which implementers are advised to accommodate.
Radio time-slot scheduling is a complex issue, concerned with determining when the radio is and is not available for use. Some aspects of scheduling fall within the scope of the Bluetooth Core Specification. Issues relating to collocation with other radios and other considerations and constraints, such as those which an operating system might impose, do not. A feature known as Slot Availability Masks (SAMs) is defined, however, and this allows two Bluetooth devices to provide information to each other about what time-slots are available for use and by taking this information into account, the scheduling used by each device may be optimised to avoid using time slots where collocation-related interference is likely.
The LE Coded PHY
Bluetooth® LE offers three different ways of using the radio. The three alternatives are part of the physical layer and each is referred to with the abbreviation, PHY. The three defined PHYs are:
-
- LE 1M – 1 Msym/s symbol rate
- LE 2M – 2 Msym/s symbol rate
- LE Coded – 1 Msym/s symbol rate with Forward Error Correction (FEC)
The LE Coded PHY increases the receiver sensitivity so that a BER of 0.1% is not encountered until the receiver is at a greater range from the transmitter than would be the case with the LE 1M PHY. LE Coded is used with a parameter called S set to either 2 or 8. When S=2, LE Coded approximately doubles the range over which communication is reliable. When S=8, range is approximately quadrupled.
Reliable communication at a longer range is accomplished by the LE Coded PHY without increasing the transmission power through the inclusion of extra data in each packet which allows errors to be both detected and corrected using a mathematical technique called Forward Error Correction. The increased range is accompanied by a resultant reduction in data rate, however, with S=2 yielding 500 Kb/s and S=8 delivering 125 Kb/s.
The primary purpose of the LE Coded PHY is to increase range, but it does so by reducing the bit error rate at lower signal strengths so that communication at longer ranges is sufficiently reliable.
To learn more about reliability in Bluetooth® connection-oriented and connectionless communication systems as well as how to achieve reliability in Bluetooth mesh networks, check out Woolley’s in-depth paper on Understanding Reliability in Bluetooth Technology.
![]()
FEATURED DOWNLOAD
Understanding Reliability in Bluetooth Technology
Download this detailed discussion on reliability in wireless data communication and the techniques Bluetooth technology uses to increase reliability.