Security is a reoccurring concern with new and even existing technologies, especially as we draw closer to the Internet of Things (IoT). Benefits like flexibility, energy efficiency, and interoperability are moot if user and provider data is at risk. While most technologies boast enhanced levels of security, what does that mean in a Bluetooth® Mesh network?
Security is at the heart of the Bluetooth® Mesh networking design, and its use is mandatory with every packet encrypted and authenticated. In most Bluetooth technology applications, you can customize your network security when developing your product, which is common when only a single device connection is used. However, since a Bluetooth Mesh network is built on tens, hundreds, or even thousands of devices communicating with one another, security of the entire network requires additional measures and methods.
Multi-Layer Security
Security in Bluetooth® Mesh protects your network against various threats and issues on multiple layers. These include replay attacks, which are prevented by judicious use of sequence numbers; man-in-the-middle attacks, which are protected against by using asymmetrical cryptography, such as the Elliptic Curve Diffie-Hellman (ECDH) key agreement protocol, during important procedures; and protection against trash-can attacks from discarded devices by ensuring security keys get refreshed when necessary.
Bluetooth Mesh is the only network topology built around mandatory security keys, which secure the network at multiple layers of the stack.
- The device key (DevKey) authorizes you to provision and configure a node so you can add devices to your network
- Application keys (AppKeys), unique to Bluetooth Mesh, allow you to secure messages relating to specific applications, such as lighting, physical security, heating, etc.
- Network keys (NetKeys) apply to all messages on the network so that nodes can securely communicate with one another
Blacklisting Potential Threats
If a node is removed from a Bluetooth® Mesh network, the device and keys it contains cannot be used to mount an attack. You can add that node to a blacklist, which keeps it from receiving new security keys during a key refresh. As such, a node that was removed from the network, which contains old security keys, is no longer a member of the network; it poses no threat and can’t be used for trashcan attacks.
Security is at the heart of the Bluetooth Mesh networking design, and its use is mandatory with every packet encrypted and authenticated.
Redundancies on Multiple Fronts
In a replay attack, eavesdroppers will intercept and capture one or more messages for retransmission later. This can trick the recipient into performing actions from an unauthorized device. A commonly cited example is a car’s keyless entry system that is compromised when the authentication sequence is intercepted and later the message is replayed to gain entry to the car.
To prevent replay attacks, a Bluetooth® Mesh network uses two network PDU fields: the sequence number (SEQ) and IV Index. The SEQ value is incremented every time a message is published. A node will discard any message with SEQ value less than or equal to that of the last valid message, as it could relate to a replay attack. Similarly, IV Index values within a message must always be equal to or greater than the last valid message from its source. This security redundancy provides an added level of protection.
Reliable, Secure Connections
The IoT is fast becoming a reality. From beacons to wireless lighting platforms, we are already seeing the initial phases of IoT deployment. The demand for reliable, scalable, and secure wireless connections is paramount to supporting the next evolution of IoT solutions. Only Bluetooth® Mesh offers the industrial-grade, government-grade, multi-layer security that the IoT demands.
For an in-depth look at Bluetooth Mesh cryptography tools, check out the Bluetooth Mesh Security Overview.

![shutterstock 1653733096[1]](https://www.bluetooth.com/wp-content/uploads/2024/03/shutterstock_16537330961-660x372.jpg)
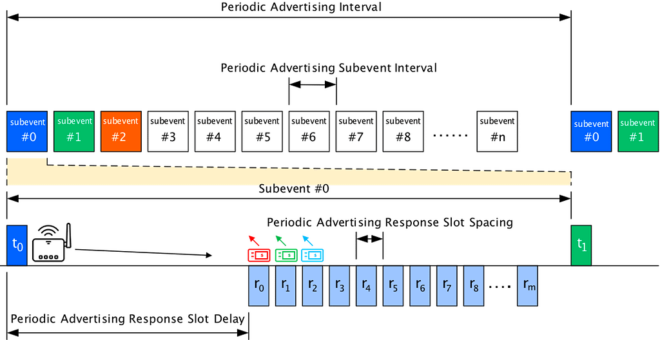
![Periodic Advertising with Responses[1]](https://www.bluetooth.com/wp-content/uploads/2024/02/Periodic-Advertising-with-Responses1-660x345.png)